Fraud is a global problem. Last year alone, a report says consumers lost US$56 billion to identity fraud. And the problem isn’t going to go away anytime soon given that phishing, which is the first usual step to committing fraud, remains a top threat worldwide. But like other forms of cybercrime, victims have a choice to fight back. Organizations, regardless of size and industry, can use tools and capabilities that aid in fraud prevention.
How Online Identity Fraud Works
The typical scam leading up to identity fraud begins when targets receive a phishing email, text (smishing), or call (vishing). The potential victims may then act on the message and are led to a login page. When they enter their username and password, these are intercepted by the cybercriminals and kept for their use.
The message in such cases can be a bank notification informing the victims of an incident that they can only rectify by logging into their accounts at the soonest possible time. Here’s an example from Wikipedia:
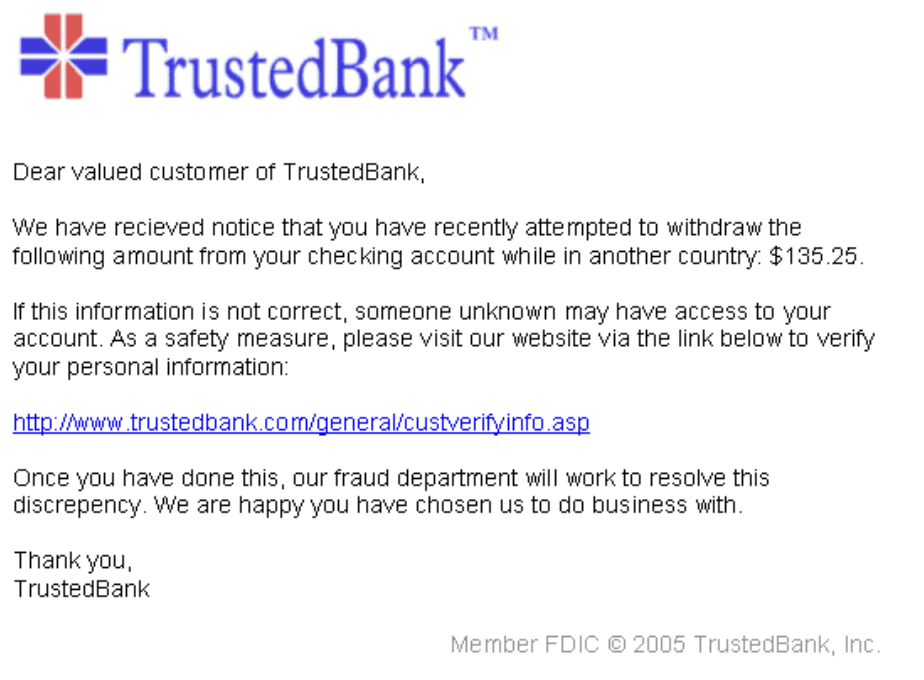
Scams work because the perpetrators exert a lot of effort to make the messages look very convincing. The attackers find out what banks the targets have accounts with. They mimic the banks’ logo and sometimes even copy official communications. But the links never point to the banks’ official login pages but to fake ones instead designed to steal their account credentials.
When all of that is done, the cybercriminals can use their username-password combinations to log in to their banks’ real login pages and steal their money using their identity.
But as we said, there are ways to combat online identity fraud.
Possible Solutions to Detect Online Identity Fraud
Identity fraud cases don’t affect just the victims who end up getting phished but actually cause greater damage to the banks and other companies that get impersonated. Why? Because so long as the people whose identities were stolen prove they were scammed, the banks may be obliged to give their money back.
Several best practices can, however, help if organizations make them part of their cybersecurity strategies. Three of them are listed below.
Check if an Email Could be Malicious
While most malicious emails can look very similar to what you would normally receive from service providers (e.g., banks, couriers, etc.), there are always hints of ties to malicious activity. Look closely at the email domain. Is it the same as the bank’s official domain name? Did the sender address you by your name? Are there tons of mispelllings and grammatical errors in the message? Is the email urging you to click a link to log in to your account or else you’ll be locked out? Is the embedded link safe to access?
As a general rule, do not even open emails from people you don’t know. And definitely don’t click the links embedded in them. Those links could take you to fake login pages rigged to steal account credentials and user identities.
Use Strong and Unique Passwords
There is a reason why online services advise users constantly to nominate strong passwords. One, complicated passwords (those that combine special characters, uppercase and lowercase letters, and numbers) that may not mean anything special to their owners (e.g., birthdays, anniversaries, etc.) are had to guess even for password crackers or guessers that cybercriminals use. Using a password manager may help with this.
Avoid saving passwords on browsers as well. That is especially true if the computer doesn’t have cybersecurity software installed. Cyber attackers can use sniffers to steal them without alerting their owners. Last but not least, avoid reusing passwords for several accounts. If one of them gets breached, the other accounts they’re also used for are likely to get compromised as well.
Employ Specialized Fraud Detection Tools
End users aren’t the only ones that suffer when their identities get stolen. Their service providers can, too. And fraudsters sometimes get away with what they’ve done because they hide behind anonymizers. Using an anonymizer detector can help banks and other organizations screen all logins to their networks.
Not everyone who contacts you via email can and should be trusted. In fact, a 2020 study suggests that one in every 4,200 emails is a phishing email. And phishing is, of course, one of the most common ways people suffer from online identity fraud. That said, the threat’s unwanted consequences are avoidable on both sides of the fence—the user’s and the service provider’s.
Laila Azzahra is a professional writer and blogger that loves to write about technology, business, entertainment, science, and health.
