You probably know that all companies, big or small, can be a cyber attack target. The bottom line is: Threat actors don’t discriminate when it comes to choosing their victims and they will use any and all available means to infiltrate networks to steal sensitive information, disrupt your business, or both. That makes it critical for all companies to determine and manage their potential attack surface.
What Is Your Attack Surface?
All vulnerable Internet-connected devices and applications are part of an organization’s potential attack surface. Cyber attackers can exploit a weakness in any of them to infiltrate a target network. And these weaknesses are not limited to security gaps in hardware and software (those typically identified by common vulnerabilities and exposures [CVE] numbers) but also include employees and third parties like your partners, suppliers, and customers.
How Do You Determine Your Potential Attack Surface?
The first step toward determining your potential attack surface is asset identification. You need to do a comprehensive inventory of all your digital assets, even those that have been decommissioned and probably forgotten, as they can all be exploited to infiltrate your network defenses. That is where DNS data that is obtainable from domain and IP intelligence sources like https://reverse-ip.whoisxmlapi.com/overview can come in handy.
DNS data can help you map all your digital assets.
It’s very unusual for a company to keep all of its teams intact. Employees, including those who manage your IT resources, come and go all the time. And sometimes, when system, application, website, and network administrators resign or retire, process turnovers can go awry. That could result in forgotten devices, programs, or web pages that threat actors could easily hijack.
DNS data, specifically from a reverse IP/DNS lookup, can help you keep track of all your digital assets by simply using your IP addresses as search terms. Say you own the IP address 8[.]8[.]8[.]8. Keying it into a reverse IP/DNS lookup tool will tell you that it resolves to at least 300 domains.
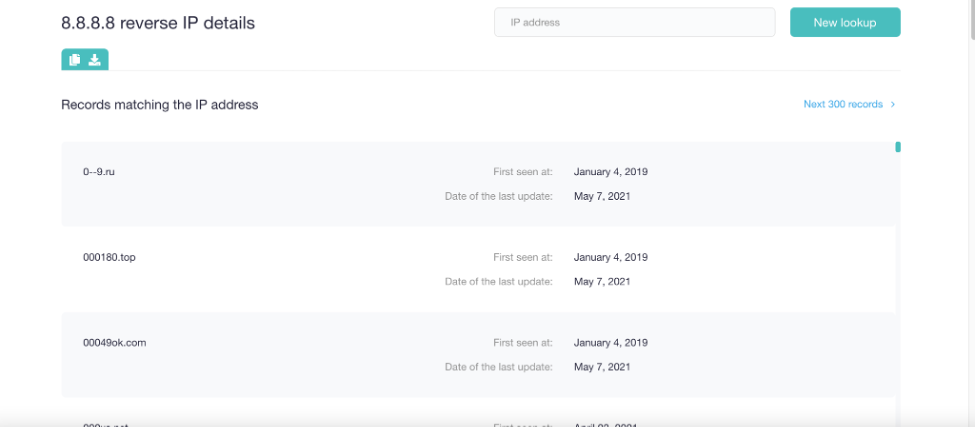
If the IP address is dedicated (meaning you’re the only one using it), then all the domains on the list are part of your network. Note that DNS records, which point browsers to the pages users are looking for, require regular updates. Why? Threat actors often look for forgotten domains and subdomains so they can point these to their specially crafted malicious sites or pages via DNS hijacking attacks. The last update date indicated beside each domain name on the results page will tell you when an update was last recorded on the DNS, and thus which pages may need updating or deleting if it will no longer be used.
DNS data can help you avoid sharing malicious hosts.
Security vendors (through their blogs) and news sites publish indicators of compromise (IoCs) regularly. These serve to warn the public about domains, subdomains, IP addresses, and files they need to steer clear of to prevent network and data breaches. Most if not all organizations monitor these, along with well-known blacklisting sites, as part of their cybersecurity strategy. And access to all identified IoCs are typically blocked to prevent risks.
If your IP address gets included in such a list, chances are your website visitors or customers won’t be able to access any of your business pages because their security solutions or even browsers would give off alerts. That translates to a tarnished reputation and lost revenue. Reverse DNS lookup tools, however, can help you avoid sharing malicious hosts.
Let’s say you use the IP address 35[.]186[.]238[.]101, which has been tagged “malicious” on VirusTotal. You can use a reverse IP/DNS lookup tool to see which web pages (including yours possibly) may have been red-tagged as a result of the connection with the IP address.
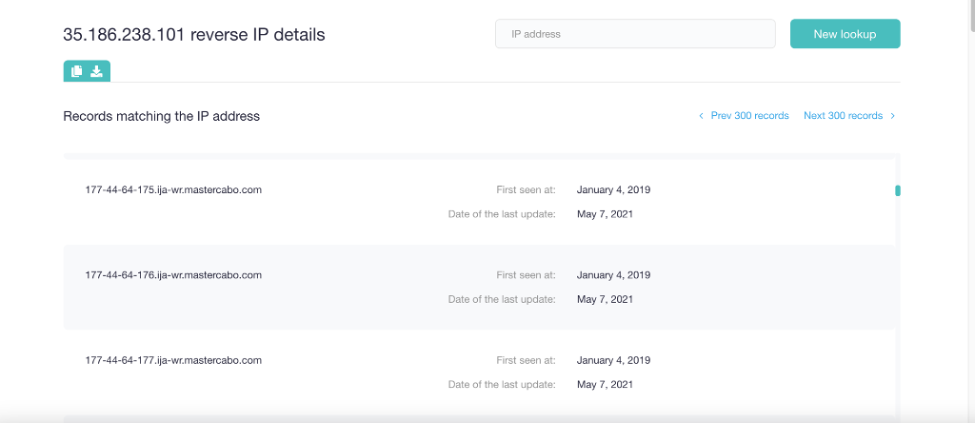
This process is especially useful for companies that use shared hosts. After identifying all affected web properties, you can ask your Internet service provider (ISP) to assign you a different IP address, one that isn’t dubbed “malicious” anywhere.
—
DNS data has many more useful applications for reducing your company’s potential attack surface. You can also use it, for example, to identify all domains that resolve to a malicious host so you can avoid accessing them for utmost security.
Laila Azzahra is a professional writer and blogger that loves to write about technology, business, entertainment, science, and health.
